In what is being perceived as the third major ransomware outbreak of the year, a new ransomware infection called Bad Rabbit has hit parts of Eastern Europe and Russia. The ransomware targets this time have been high profile. It first started infecting systems on 24th October and has been spreading rapidly ever since hitting several organizations simultaneously.
Where has it been detected and Who’s the worst hit? (So far…)
A multitude of organisations spanning across countries such as Russia, Turkey, Germany, Ukraine and other parts of the Balkan region have come under the grip of this malicious cyber attack. In fact, researchers at Avast have even detected it in South Korea!
Amongst the high-profile organisations that have been targeted, Russia’s news agency, Interfax confirmed that it has been one of the victims.
What is its Modus operandi?
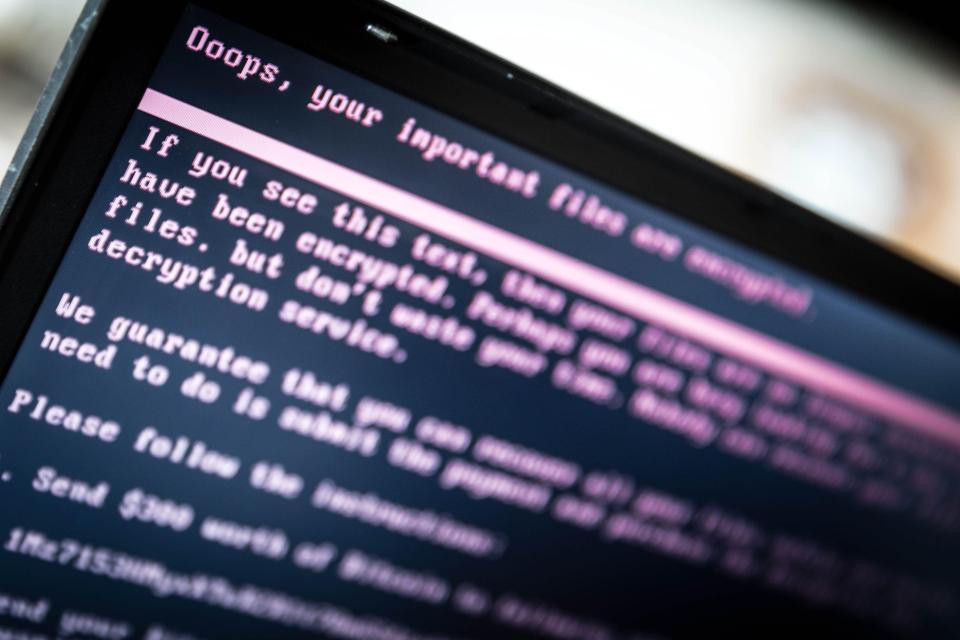
The notorious ransomware presents victims with a ransom note informing them “your files are no longer accessible” and “no one will ever be able to recover them without our decryption service”. Then, victims are directed to a Tor Browser page and therein demand a ransom worth 0.05 Bitcoins or roughly $285 with a countdown timer ticking on the side of the screen.
Unfortunately, the people who fall prey to the vicious ransomware have no other option left but to pay the amount.
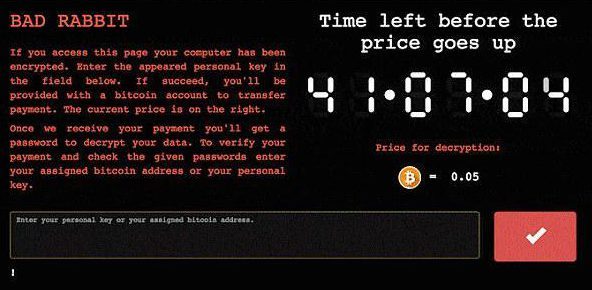
Picture Credit: The Independent
How does it spread?
It spreads through a fake flash update on compromised or vulnerable websites. The ransomware spreads its code by luring drive-by downloads on hacked websites by displaying a pop-up on the screen of vulnerable systems. The pop-up asking for a flash update is actually a malicious install! Beware.
Who is behind it?
At this time it’s not perfectly clear. But, going by the patterns of the previous Petya ransomware attack, it seems the same group could have carried out this attack. And, since the cyber attack primarily hit Russia and Eastern Europe, there is a growing suspicion the perpetrators could be from the same region.
How can you protect yourself?
This ransomware has once again followed the pattern of targeting Windows systems. Researchers argue that those who fall prey to malicious ransomware need not pay the ransom since it will encourage more such attacks.
But, according to Kaspersky Labs, users and organisations in general need to be proactive. Kaspersky says users can block such malicious attacks by blocking the execution of the file ‘c: \ windows \ infpub.dat, C: \ Windows \ cscc.dat.’ and simply prevent the infection of their systems.
SEE ALSO: OnePlus 5T specs and design leaked! Here’s all you need to know

